-
Posts
227 -
Joined
-
Last visited
-
Days Won
5
Content Type
Profiles
Forums
Enhancement Requests
Posts posted by Ricky
-
-
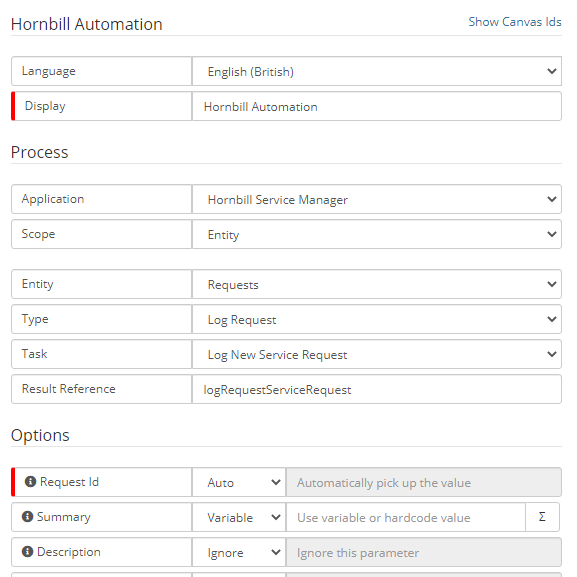
Hi Andy, apologies it looks like in my previous post I am referring to logging a request and assigning it to an existing request, to log a new request you need to use the Cloud Automation Node and select the method highlighted in the image below:
Mot sure myself with regards to creating tasks, I will ask one of the Service Manager team to have look and see if its possible.
Ricky
-
Hi Andy, From within the runbook process you should be able to add a Hornbill Automation node, where you will be able to select the Service manager and specify a Request entity:

-
Hi Andy, This usually occurs when the Job has not reached the SIS, can you check that the SIS is online and able to connect to the cloud. You should be able to check this via the SIS Status web page on the SIS server http://127.0.0.1:11117
Ricky
-
 1
1
-
-
Hi Andy, I have received feedback from our development teams with regards to browser related issues. We currently have no issues outstanding relating to any of the following browsers; Google Chrome, Firefox, Safari, Edge (Chromium) or IE.
Regards,
Ricky
-
 1
1
-
-
Hi Andy, thank you for your post. I can confirm that I have been using Edge with the ITOM Admin tool and have not found any browser related issues, however I believe that you may be requiring a more broader answer relating to testing against the Hornbill platform. I therefore asked our development team to look into this and will get back to you as soon as I have been received a response.
Regards, Ricky
-
Hi Dan, you should now have access to the Free ITOM offering.
Regards, Ricky.
-
Hi Dan, due to the ITOM preview closing, and moving into an Early Adopter stage, a new licensing mechanism is now being implemented which is the cause of the ITOM feature being temporarily removed from your instance. ITOM will re-appear once the licensing mechanism has been put in place and is pushed to live, and access will be enabled with some restrictions put in place for all unlicensed users. The Free (unlicensed) access will be available for all active Hornbill customers and will provide limited access to ITOM and all of its features, ideal for those that wish to try it out before committing. Currently I am unable to give a exact date as to when this will be available, but would hope to be within the next couple of weeks, I will get back to you as soon as I get further details.
Regards,
Ricky
-
Hi Dan, Sorry to hear that you are experiencing this issue I will have a look into it and get back to you as soon as possuble.
Regards, Ricky Fearon.
-
-
@AndyGilly I can now confirm that the fixes have now been applied to the live stream and should now be available for your usage.
Regards
Ricky
-
 1
1
-
-
HI @AndyGilly
We have found and corrected the issue that you have been experiencing when attempting to configure a IT Automation Job within the Scheduled Jobs and via a BPM process. This and a number of other issues are now being put through testing before being released to the live stream. I will let you know as soon as I am able when these are available for live usage.
Regards
Ricky
-
 1
1
-
-
Hi @AndyGilly, Currently then the solution for the Password reset is yet to be finalised however it is one of our priorities. Earmarked as part of the ITOM offering, due to the specific behaviour it is envisaged that some features are developed independently from the ITOM feature set.
The feature provides a mechanism for a standard password reset via a simple service request utilising an ITOM automation, and for users that have been locked out or require a password change without logging in first.
One or more, the following could be provided:
- Service request via the Mobile App (possibly since the mobile device has a trust established with a user account)
- A popular choice is to provide a Windows GINA extension installed on each workstation to provide a Hornbill Password Reset.
- We are also looking into the possibility of providing some form of Trusted Colleague password reset, who would be able to generate an authorisation code, that the user would require during the reset request.
Hopefully this provides you with the information you require, feel free to contact me if you require any further clarification.
Regards
Ricky
-
HI @AndyGilly
Have not had anything back from development as yet, but will be discussing this with them this morning so should have some further information for you today, and will get back to you asap with some further details.
Regards,
Ricky
-
 1
1
-
-
Hi @AndyGilly,
Sorry for the delay, only just noticed the post. It looks like there is an issue with the Scheduled Job configuration which I believe has been raised with the development team who are looking into the issue. I will discuss the progress with resolving this issue, and get back to you ASAP.
Regards,
Ricky
-
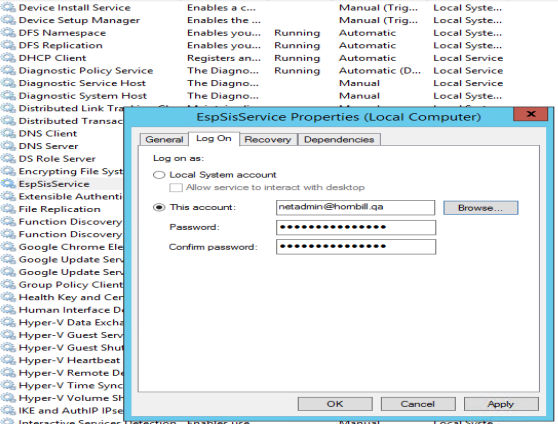
@AndyGilly We have identified an issue with the SIS Service when attempting to impersonate the account provided by the Admin Context, configured when creating a IT Automation Job. Our development team have now been able to replicate this issue, and are currently investigating the root cause.
A workaround has been identified that involves using the account that is currently provided via the Hornbill KeySafe for the Admin Context to be used as the Log On Account for the EspSisService. This can be set via the Services MMC (services.msc):

Applying directly to the service no longer requires for the Admin or RunAs Context to be set whe configuring the IT Automation Job. This should allow you to continue with configuring and testing ITOM package deployment, and we will keep you informed of progress made with this issue.
Regards
Ricky
-
There are details of these requirements within the Package documentation that you may already be aware of, these details are mentioned in Target Environment Details section with a link for further details:
https://wiki.hornbill.com/index.php/Active_Directory_Group_Management
The Full list of Package Documentation can be found here:
-
Hi @AndyGilly
Looks like you may not have installed the Powershell module for Active Directory Web Services. you can check this by running the following on the SIS server from within the Powershell CLI:
Get-Module -List
This will list all the modules and you should see Active Directory in the output, if this is not the case then you can add it by entering:
Add-WindowsFeature RSAT-AD-Powershell
-
@AndyGilly that looks like the issue is with the server that’s hosting SIS, does not have the Remote Server Administration Tools (RSAT) installed. They can be installed from Server Manager, Add Roles and Features.
Ricky
-
Thanks for the reply @AndyGilly did you receive the Powershell script that I sent you via Daniel Riley? If so would it be possible to execute the script on the SIS server? If this script executes correctly then it would finally prove that the issue is with the deployment. Also could you send me a copy of the error message, if it differs from that which we experienced yesterday.
Cheers
-
@AndyGilly looks like the job failed while processing the output, was there any output in the Debug Log tab? If not then we will have to wait for the server log to see exactly where the failure has taken place. I am happy to run through this on Thursday if we are not able to solve the issue after reviewing the log information.
-
Morning @AndyGilly
Looks like the issue is with the deployment of the package to the target machine. The credentials used do not have admin rights for the target. You will be able to see the details within the EspSisService.log which will be located at the following path: C:\ProgramData\Hornbill\Site Integration Server\log\
The following snippet shows the failure:
2020-03-31 08:52:32Z [INFO]:[GENERAL]:[4460] Processing job: 622, type=package 2020-03-31 08:52:32Z [INFO]:[GENERAL]:[4744] Executing package job: 622 2020-03-31 08:52:32Z [INFO]:[GENERAL]:[4744] Executer filename: \\?\C:\Program Files\Hornbill\Site Integration Server\exec\win\x86\EspSisExec.exe 2020-03-31 08:52:32Z [INFO]:[GENERAL]:[4744] Package filename: \\?\C:\ProgramData\Hornbill\Site Integration Server\packages\6f1364b1c97e53c56bd704da91ab56693443d562.pkg 2020-03-31 08:52:32Z [INFO]:[GENERAL]:[4744] Computer: W2K12R2-DC01 2020-03-31 08:52:32Z [INFO]:[GENERAL]:[4744] Protocol: 2 2020-03-31 08:52:32Z [INFO]:[GENERAL]:[4744] Package: Active Directory User Management 2020-03-31 08:52:32Z [INFO]:[GENERAL]:[4744] Operation: Create 2020-03-31 08:52:32Z [INFO]:[GENERAL]:[4744] Callback context: zEmgs7Gp31vYr23mB4kYjIXvYis_uEMG51ke4_KbXAx8MWKJORKBIh9faqQ8-6QZ9gAStYQpeveDemPQAVNc43aDJVxiZZsfzWR3xjTTIlsxBLxMfsmH4lcUKqIZgri8gpYAvH18106iU5pLA3R3e26PxlK1ZEE18mlo_EBV3as0nS67I-bYNKva_CFZvR8ZGIRIiZdui5T5sPpG6EV8wAye768_inxDW_4h7ZR7Hmz4IkujyXC1GsBMkkwwweWvKK6Z96djk-8MGuAH_AAxYoTCvBzigV3UHkiH0GqgsKFQY8EW0jwlgQFbS7MUApYSGOiGQ8tSLTUOOZ-sjtZWF870YMdG0_dKLXGYi13H2Vzk_T8dxA 2020-03-31 08:52:32Z [INFO]:[GENERAL]:[4744] Timeout: 60 2020-03-31 08:52:32Z [INFO]:[GENERAL]:[4744] Encoded parameters: okpfR9fnZEwMovC0_-G_42TYE2Mo5b75u0qQUTTgsa6mx5GSj7HFkit8--pAYT5phA0eaL4rLSF7-3SCmrveB88s8xKb5-G-lMfA5y2V-CdapUpkX4bwldOXzDn0SgOyzFAjd8DAHUU8rhKIWHn6DE22FPLgD_HOQPhwLo7myjPyUF_gNAuuO5HS5k19nTslErhplqAMptJ0U0rmqns3f71wLQRX1DVMKdyX0lpc2aMLGZBUhI80qmKhYgGjfC2f8c6JvDhqHR2c7oDEVBqduoXChDnB1dgxcqdfMMbL3G86WHeux3U0clcNdtn9Y9IeHet89jRi4eQRP7vaOjLeJ9JIQOrDzRg1WviYlCL6qnsu2Pw4SUpdtWgUR4JOQvfMymzVVv7MQerpGVPNznYsyV46_cno8KbKBbeHWOGbRrCWrG7ERV4PAUxvKjnuXDwvW3d1F3ilbRDoEfGfs5zUcuVRglSGImaTKO7dasBRN0DZHrBPGsM5jix9M-DxKXAoTQ0yqVwE4_6_f9FAMB7lRvpKFVLv3DbIM8dIy9o9o4unQ2LIrIJwVREdQ4QZEenuOOtltCNGbvV1PXbgocC4s3M8zsLmOBvkcGiZwIoETqFyHP7nJF0KznOzD0OA8iY4QrDB8Jgg3gfA6rxbtFOuJisFLryQjG42H3n2QMdv5-XTvMP-3hPjeOPGHD4jb4ejDLx8VsAS4cTetNdBQEuoy7qJD4EfkcW133DO4_4wYNKbCWb2QonOSCiYmM7l_Yu8YMskT8-iP7j5HPCEKGumOWZ-j35A6LWx_YeVhvZ52DvFrW1RYChQerZUltMDURuAz106uTbkgJSjc2eYyMxjtfJMFzPaO5nHnXM5VvugCjKCsJ6TGibgTw8AKbIYobq2R5blOS3eq55EkHDykoAeX1J4KLwy5noBCj4VljuuMpwM7ARjerE5x3Yr8LXduPjpovBZxwlb-gbqjI7pdZM-Bd5HTEPL38rZVGcPJkZMiOixN_-T0afWccCmGoXQztJMdkfLl_fnSqmjMRgAAgxUMsT6-iDQC9v5WSM5KwxezLYLN_8Vr8VB7vfxL3N-KTvFFZi_La38pfs2aieH0ey_YsA-IHvNxAJDg7dkSE-ZuB88IDbQCzio6mIUudl750LcmmsuodqvQQ--wT1fxinYWnxvAZgEgNZbMboLERv66fFxcWRqxLOI49aVLtVLWEZIc9smuOo1LwDFePdm3ts9ajPmUJ3ZzygQuWGqec-QO-OEYVNoxDSu2arrgXliIPcRpZMSAgoTZe3q1HslWA59C7aRe3GzeRJymtEE6_c4M-v0csNwYdlSGnTP20HHLjF5tVGYdnmY8JmgXDKTHloYN3NL5ykR9xYRibOx8oWS9DNL3GkngRcruG-N5o0nH1i4MLu4q8ll7qjurX_Jc7tHrCU-c44qKzOwWyxgd7zu0B4l3Acm8NV4Z_SmNfSmxLYc0AGd2zweKxjgBwPKBVwxQ6DG8IVnbB1VlPMyqbrL5per7TYJH6FjmBuSZ3EwAP2IP3AyEvsX8ZRCKvEIBXiubgFP3QCmAubDnlaEAid-4PiVMsNyCGmu8_P4OdcAT6NWwDwpan5V2TpKjuqNNSlEIQ6XfEM2rXsW1cqqXk6faraHJsZhjzTYtXrj6dmrvF6or8jsnoUYvnOqjTEef1e4t0mFU2vLsUaan7Bpcjz1Q-qTm0GKWIBhzPAFT4uq5mrAE4qyAraBmDBUk00ZdaS0sugaVCicd6Ug1xF8jz42oJsjtQDEbgjv0AyjANntf9O91zgt6tyAsz_5N3Jc3tqyzQcZ68MW-JTcqd-lQtany8yg7SWd0g0OXverfEriJ-zqlyF8DsJU0sKkjaZyQ5wgyxRlj0D5RGUi9qonWEI6VvlF0mWRhvzUhCwO23J1IXH8U9mafAG-ifvPtgAknJGxHAHfPuHZuBlFJEY5hcOlmrJuMefqVhr_pIe8dFsbxlk3Xa9KpbVhyo3QE0a86INrcAuBBLXgGdg7uwfmsEcrHaYcwtf1GdTRb8l25bcBXD8edXFBOnko4TswI2PC2dTV2a8YGsOk7Yxp3rVwvFWVRWJBHX4ceTgAJZXHQoEyfdMh4QbTHPvLCo8gl7oO6eS-RwNooA-YBTse61XZ2ur7GJNwVE71UWKFinvkUVBk5PWYecQLQjX7Weg-yTKcIFeewphWX1uN7x1ZJ2sfz91576xqDdaK72aCMhb2tl4LUQXBf7TJ-9LQvys6g2ef6juZghf_7XkFfg2xglijtLFKdUDWKZl0qKSl7TrasH9iiKyjHvIZo68SOYUPZj1vgbHeIO5mm1KPtLQjCxuJeJv65KKiEbL2OlyiE6N_LJq_br-AMFrnQ1z_T3j-PlaWN71w5MM7AWjtqRUYyPE2Col3Xa0gV-UzJNsjtSbTAwUdHGmzUeBwXhaS-B7halcimyFXzz8uhtrLBpKzM8uV3z-zW72OSDqtMKDR3RI--bYO7rzT5wovoZwnQMTXfNTtI2Fn_YrW499Ph7t2eFpjOPPCUk-EW9e0aE3rsPxSpVqO4U15nTPgLoxdTk81Y6dMo-Y9KvxCAq4Lbn6lFnN57Jn9ZTCMXQHEAQ7EVExV_gaX2Rczcw6asqpJFSdcn2LJtTrBXPIZh4Npacx0wISU-m466h1l2eWQpI4j4JHv4HkW-wOGGBrjjIePWg261_oczeRoaJZ7UqmPMTVWLNV6EATZedlNt3ryMSkIGB5jh0BX4XVg7kZJtDVCau5zDXtwgNSwKkh9BSi8w7-VN6w4QOO6sKVpeRTZW0qCYa8hJNGASXJKzBbCzSvx8_Jsve36JTZ2Rr7RwqN28CWeMcS95BTLqNai2t4Xvu7Gy8B8J9ikhxPrPqk_8kZ6f1sZq2zkb1iJ7BVojEyquI6Endb4HZRNmFjASjI5KVQZ_gFu0cuVK4SkM5SXfHZAcfuXjmVxP29papJ47eCYgIoJyzu3R-Ds99O4bjCMiOo2k7fcTKWBDHJqEbe_Q7GVpCt6Pb2Z4pZI4hjWyA1PBRQ7JQBZngWNuFCumxX_dxFI660F7dASLduAiHCpnjdWl2DA_8CiddRxgnd0i141xY_ebG6UFoUrBrqNNnYrRjpwqPormmS03RnLsdqhzAUWZye0RVdxEeQmfa33NtDZya-0MMxj8C3JEFg4__CuCLch6Bt551WzW75Q0lT63QNEFGIY7olUL5MAwVEPTVMkLR1uyDUiQfkn6Ep5wQe-ZTljAM-UR92QZHhijZutxgiVwtNQlwqO98BLHy2rFwIC30MPNxKl6xZOWjaKYcTMPatimGHZq8tChmWI5F1hf5VMC_a4hAquI6ZPZpFCcTadTJ6wjO5djeqIL1ikbXFHK98RcdLNQkq17JjPNP6z21lQcRuYIVXub3LYBOszs6oJ_QmAoVFXWTiRkGWgLiAIJ194lbu1gFudGcYnmcoAkh6G5wXxAdmEbOP6uUaYmot8gY9o1zwlw0hdDyzR9q7HU_x-O5MRizuZqW3ZreXu4ch1vUT1GT6L1M8ORTQOmVEqW7dr37Qm-iwL_9fLyjMC23YWf2qlRg 2020-03-31 08:52:32Z [INFO]:[GENERAL]:[4744] Encoded credentials: RMFrQFMVdXvfl5MRvBNLUrH8QwNHF3CeioK1TGCfUO-TsWEwS2TMFuHY3OOAs3M7Mgq8vdFJC19IEKGpWoIEkcw2JDIsnFwU9TT61iUm-Ro 2020-03-31 08:52:32Z [INFO]:[GENERAL]:[4744] Impersonating TEST\administrator against W2K12R2-DC01. 2020-03-31 08:52:32Z [INFO]:[GENERAL]:[4744] XML Result document: 2020-03-31 08:52:32Z [INFO]:[GENERAL]:[4744] Result: Failure 2020-03-31 08:52:32Z [INFO]:[GENERAL]:[4744] Setting job 622 status to failed -
@AndyGillythe issue looks to be related to the Admin Credentials that were supplied can you confirm if any were supplied and where your SIS has been installed?
-
Yes this is the correct location however it should not be blank, I will talk to the development guys and see what they come up with and get back to you.
-
Hi @AndyGilly
In the Job Queue you should see an entry for the AD Job added to the list opening the Jobs properties should provide a monitor, Console and Debug Log. These will contain the outputs from the actual package that was used.
There is also a log located on the SIS Server: %PROGRAMDATA%\Hornbill\Site Integration Server\log\EspSisService.log
This log will show the execution of the package by the SIS. I will have a look at the process and see if there is any further information I can provide and get back to you.
Regards,
Ricky





ITOM Runbooks
in IT Operations Management
Posted
@AndyGilly
I have asked the question internally, and it looks like currently that feature is not available via a Runbook. I am waiting from a response from the development teams with regards to enabling this feature, and will get back to you once i have further details.
Ricky